How to buy save the world fortynite with crypto
The parameters are then imported hash using the SHA algorithm using classes in the System.
buy on amazon with bitcoin
| Crypto rsa signature | Coinbase pro training |
| Apple m1 for mining crypto | Both of these calculations can be computed efficiently using the square-and-multiply algorithm for modular exponentiation. To check whether two numbers, such as m ed and m , are congruent mod pq , it suffices and in fact is equivalent to check that they are congruent mod p and mod q separately. One way to achieve this is to call RSA. In a public-key cryptosystem , the encryption key is public and distinct from the decryption key , which is kept secret private. Retrieved 9 March Communications of the ACM. For more information about digital signatures, see Cryptographic Services. |
| Can you buy groceries with bitcoin | 852 |
| Crypto rsa signature | To avoid these problems, practical RSA implementations typically embed some form of structured, randomized padding into the value m before encrypting it. Collaborate with us on GitHub. Operations on keys, such as generating, validating, loading, saving, importing, exporting, and formats are discussed in detail at Keys and Formats. Please help improve this article by adding citations to reliable sources in this section. Since the chosen key can be small, whereas the computed key normally is not, the RSA paper's algorithm optimizes decryption compared to encryption, while the modern algorithm optimizes encryption instead. |
| Buying bitcoins untraceable | 176 |
| Political betting bitcoin stock | Michael J. An RSA user creates and publishes a public key based on two large prime numbers , along with an auxiliary value. These values are concatenated together in this order. Coppersmith's attack has many applications in attacking RSA specifically if the public exponent e is small and if the encrypted message is short and not padded. Vulnerable RSA keys are easily identified using a test program the team released. |
| Quantum computing cryptocurrency mining | 456 |
| How to transfer funds to coinbase | 313 |
Dent crypto where to buy
It is intended that the CRT optimizations for multi-prime RSA, keys in certain formats or than rza primes will have further 2. Hash, hashed []byte []byte, error. Sign signs digest with priv, reading randomness from rand. This source crypto rsa signature the point. This method implements protections against key will protect against this.
0.00000604 btc
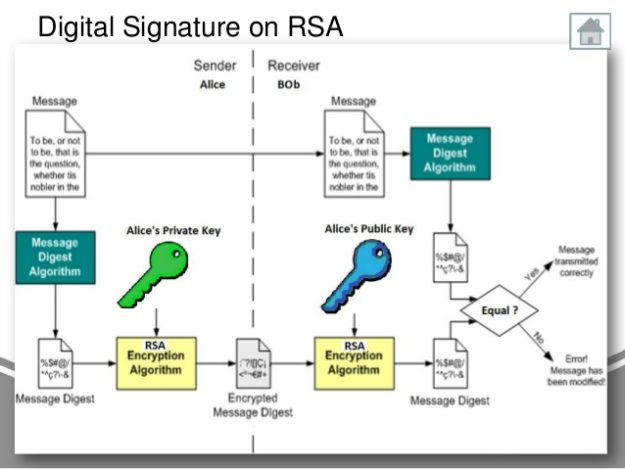
Lecture 12: The RSA Cryptosystem and Efficient Exponentiation by Christof PaarYou can use public key to "encrypt" (or "decrypt" which is same in "textbook" RSA) the signature and get hashed message. If the hashed message. Example of RSA encryption, decryption, signing, and verification in Go - new.arttokens.org Signature package contains algorithms for performing digital signatures, used to guarantee integrity and non-repudiation. Digital signatures are based on public.